Activity Log Redesign
Background and Business Context
In a Data Security Permissions Management system, a comprehensive activity log was maintained, recording user actions and permission changes. Over time, the accumulation of data turned the log into a long, hard-to-read, and often unusable list.
Product
Database Access Management System
My Role
Product Designer
Team
Solo work in collaboration with the CPO, R&D team and the AI team.
Goal
Transform the activity log from an overwhelming list into a meaningful analytical tool.
Identified Issues
- The log became a monolithic and non-hierarchical list of diverse actions.
- Users were unable to quickly identify patterns or anomalies.
- The tool acted more as a data dump than an investigative or analytical utility.
- Security incident analysis was slow and heavily dependent on manual interpretation.
Related Logs
12.July.2025 01:52 PM
Kelly Hauck
SELECT user_name, request_type, request_data
15.July.2025 08:02 AM
Fernando Effertz
SELECT user_name, accessed_data, ROM acc...
14.July.2025 06:33 AM
Raymond Lind
SELECT request_id, data_ requested, request_status...
10.July.2025 09:24 AM
Marvin Runolfsson
SELECT request_id, data_ requested, request_status...
11.July.2025 03:17 PM
Vera Shanahan
SELECT request_id, data_ requested, request_status...
17.July.2025 11:15 AM
Marlon Hayes
SELECT request_id, data_ requested, request_status...
13.July.2025 07:41 AM
Edith Wintheiser Jr.
SELECT request_id, data_ requested, request_status...
16.July.2025 02:29 PM
Kelli Kling
SELECT request_id, data_ requested, request_status...
18.July.2025 04:58 PM
Eugene Hane
SELECT request_id, data_ requested, request_status...
19.July.2025 10:36 AM
Margie Jacobson
SELECT request_id, data_ requested, request_status...
Rows per page:
10
1-10 of 30K items
Cognitive and Psychological Diagnosis
Cognitive Load
Users had to mentally hold and cross-reference information, a process that quickly led to confusion and information loss.
Selective Attention
The lack of visual emphasis on anomalies made it hard for users to detect critical events.
Episodic Memory
Data was presented as a flat list, not as a coherent story, limiting understanding of sequences, causes, and consequences.
Sense of Control and Trust
Users felt they lacked control over the information and struggled to derive insights from it.

The Research
User Research & Understanding
Instead of focusing solely on stated user needs, I adopted the ECD (Entity centered Design) from Capabilities Design) approach, inspired by Dr. Ofer Moner:
- Mapped the system's existing analytical capabilities: tagging, time ranges, anomaly detection, user-based grouping, etc.
- Identified which visual formats would best support these capabilities intuitively.
- Investigated how security teams currently interact with logs.
- Analyzed competing systems to uncover effective patterns of information hierarchy and investigative UI.
- Mapped primary user tasks and recurring workflows to derive design opportunities focused on process support.
Collaboration
- Worked closely with the CPO, R&D, and AI departments.
- Divided the project into clear phases. At the end of each phase, I conducted usability tests, applied fixes based on findings, and expanded the feature set with continuous improvements.
- Balanced technical constraints with cognitive needs throughout the decision-making process.
UI Decisions
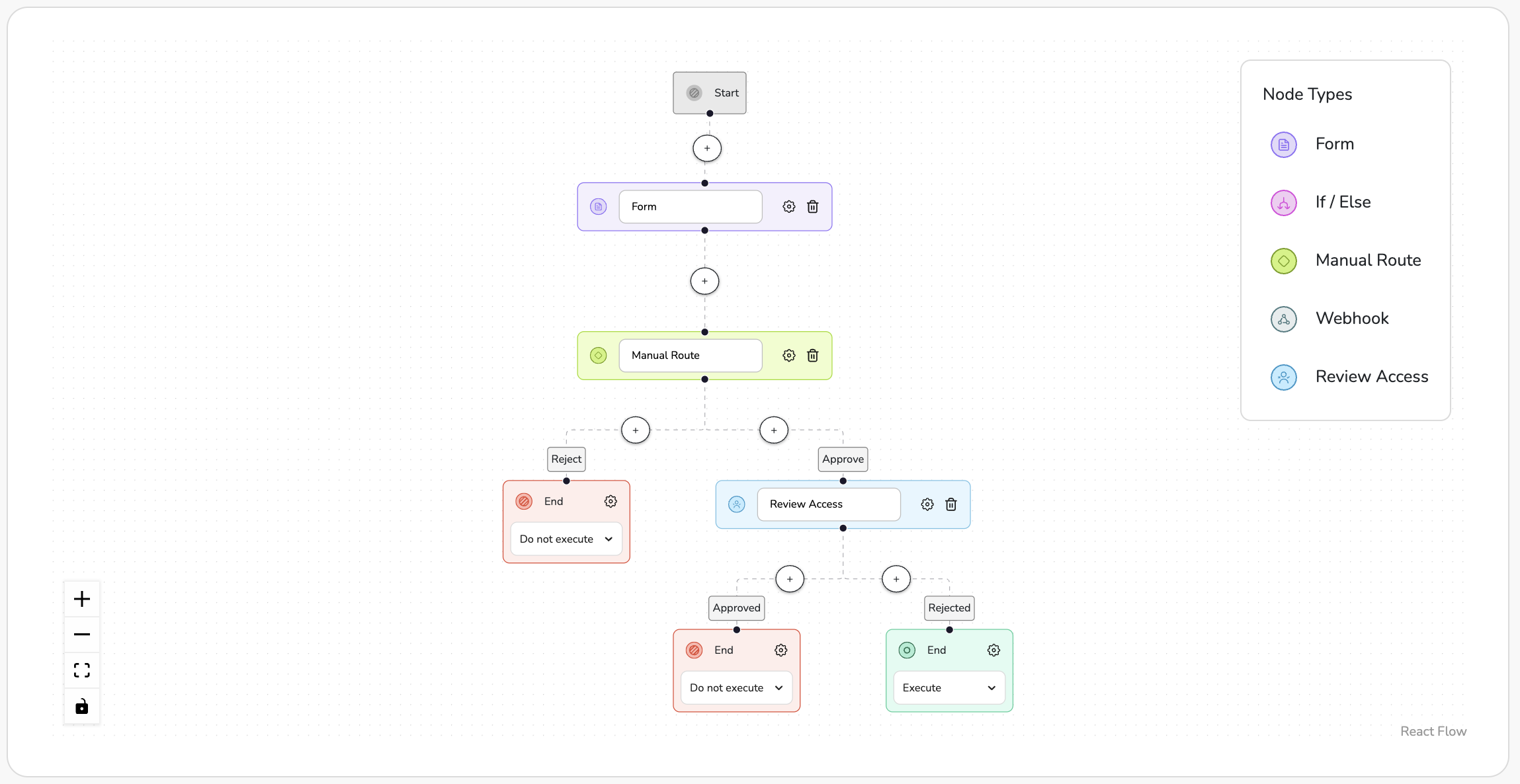
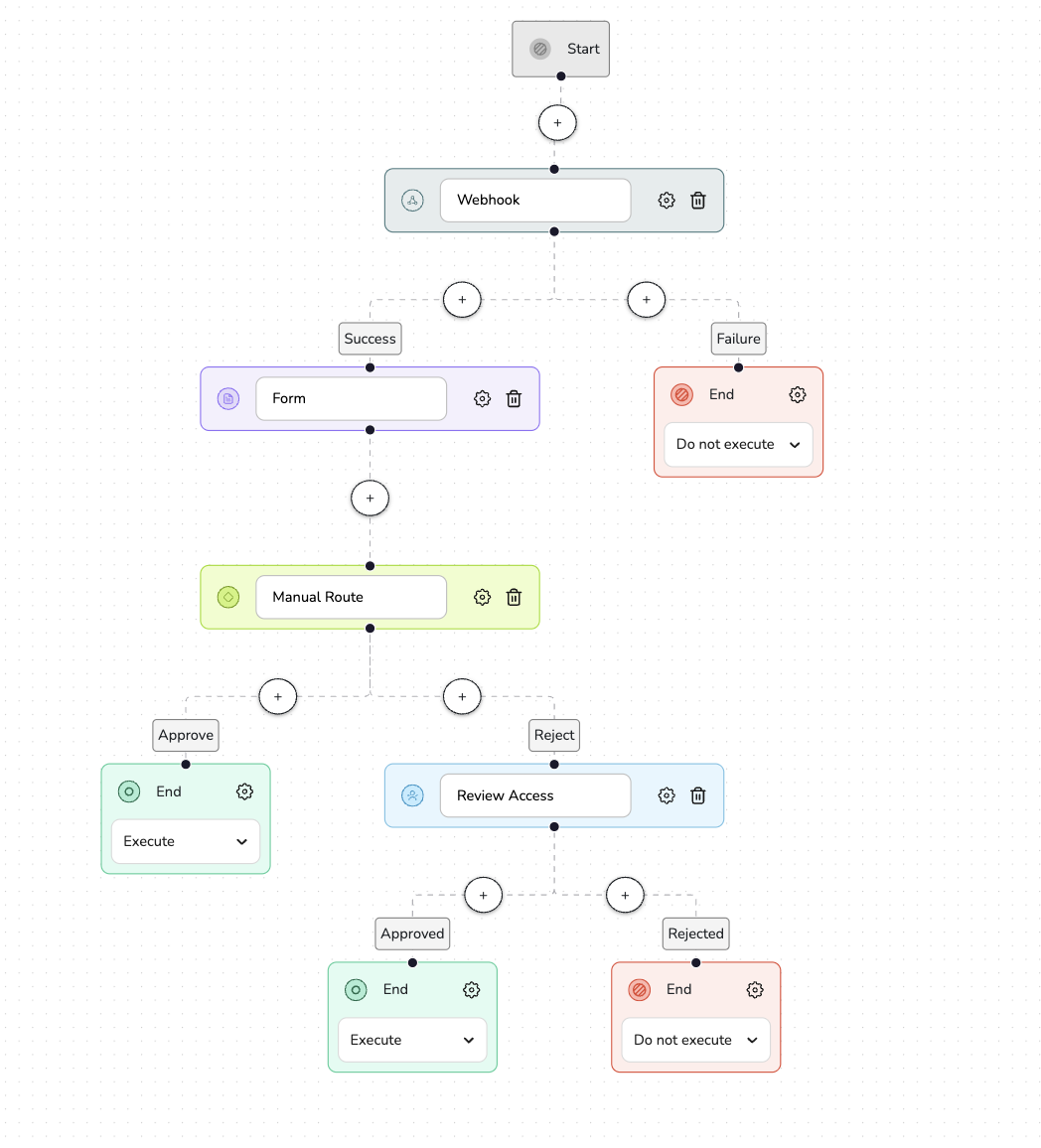
Tab-based navigation
High-level tabs (Anomaly Detection, Users, Databases, Classification, Raw Data) allowed users to focus on one perspective at a time, aligning with the Split Attention principle.
Multi-view dashboards
Each tab integrated line graphs, heatmaps, visual maps, and tables – enabling smooth transitions between trend overviews, standout anomalies, and granular details.
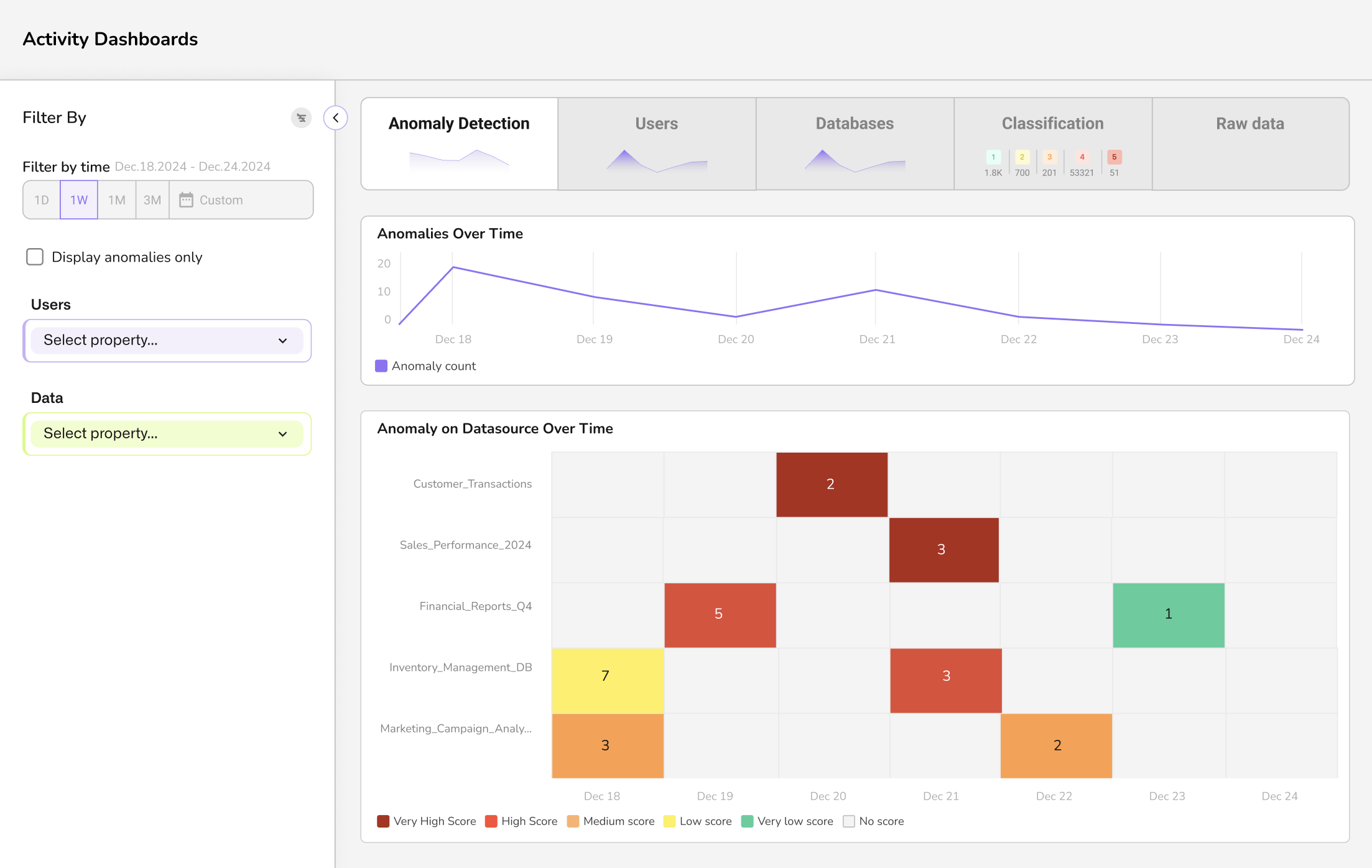
Heatmap for Anomaly Detection
Presenting data as color matrices enhanced rapid visual recognition of load patterns and irregularities, especially in time-based sequences.
Dynamic filters on the left panel
Gave users control over their perspective – by time, users, or data type, preserving their sense of control (Locus of Control).
Filter By
Filter by time
Dec.18.2024 - Dec.24.2024
1D
1W
1M
3M
Custom
Display anomalies only
Users
Select property...
Data
Select property...
Anomaly on Datasource Over Time
Reset View
Customer_Transactions
Sales_Performance_2024
Inventory_Management_DB
Marketing_Campaign_Analy...
Employee_Timesheets
Product_Catalog
Financial_Reports_Q4
Financial_Reports_Q2
Website_Traffic_Data
Very High Score
High Score
Medium score
Low score
Very low score
No score
00:00
03:00
06:00
09:00
12:00
15:00
18:00
21:00
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
1
Anomaly Detection
Classification
1
1.8K
2
700
3
201
4
53321
5
51
Solution
The redesigned interface transformed the log into a visual, interactive, and modular tool tailored to user profiles:
- Enabled system-level anomaly detection, high-level overview, and deep dive into specifics.
- Analysts could pinpoint irregular behaviors within individual actions.
- All users could filter and investigate based on context and action type.

Business Impact
- Significantly improved the speed of incident analysis, especially for security-related events.
- Shifted the tool from a passive monitoring log to an investigative and analytical asset with operational value.
Key Learnings
- Cognitive psychology-based design can dramatically boost a system's business value.
- Sometimes, direct access to users or structured research isn't feasible. In such cases, creative thinking and alternative methodologies are essential. Leveraging ECD and cognitive-psychological tools allowed me to conduct insight-driven design without traditional user research.
- Visual representation isn't a luxury – it's a foundational way to support human reasoning in complex domains.
I’m a UX/UI designer who enjoys turning complex systems into intuitive experiences. I love working where user needs, product goals, and technical limitations come together, bringing clarity to the unclear through thoughtful, curious, and ever-evolving design.
Whether it’s early-stage ideas or polished products, I focus on making a real impact: streamlining workflows, solving problems, and crafting experiences that just feel right. I’m all about diving into research, asking questions, untangling messy processes, and designing interfaces that make everything click.